This malware, the work of a new APT called TwoSail Junk, seems to allow deep surveillance and total control over iOS devices.
A recently discovered, mass-targeted ‘watering-hole’ type campaign has been aiming at Apple iPhone users in Hong Kong – infecting website visitors with a newly developed custom surveillance malware. The bad code – the work of a new APT called “TwoSail Junk” – is delivered via a multistage exploit chain that targets iOS vulnerabilities in versions 12.1 and 12.2 of Apple’s operating system, according to researchers.
Watering-hole campaigns refer to those that make use of malicious websites that lure visitors in with targeted content – cyber-attackers often post links to that content on discussion boards and on social media to cast a wide net. When visitors click through to a malicious website, background code will then infect them with malware.
Links posted on multiple forums
In this case, the campaign uses links posted on multiple forums that purport to lead to various news stories that would be of interest to Hong Kong residents, according to a pair of research notes from Kaspersky and Trend Micro. The links lead to both newly created websites set up specifically for this campaign by the operators, as well as legitimate sites that have been compromised. In both cases, a hidden iframe is used to load and execute malicious code.
That code contains exploits for known and patched Apple iOS vulnerabilities – and has an endgame of installing a custom, proprietary backdoor spyware, named LightRiver by Kaspersky and lightSpy by Trend Micro.
Backdoor
The backdoor not only allows remote execution of shell commands, but it also contains a variety of espionage modules (researchers’ names for the backdoor both come from the malware’s module manager, which is called “light”).
The modules include functions for exfiltrating contacts, GPS location data, call records, logs of recent Wi-Fi hotspots that the phone has connected to, browser histories, SMS messages, and even the iOS keychain with stored passwords for apps and websites. It also gathers hardware fingerprinting information and data about the user’s local Wi-Fi network and local network IP address. It targets messenger applications, like Telegram, QQ and WeChat, to lift correspondence from the victims.
Despite the deep level of surveillance afforded by the malware, researchers said that the campaign doesn’t appear to be a targeted effort, apart from focusing on Hong Kong residents (50 percent of whom use iPhones).
“This aims to compromise as many mobile devices as possible for device-backdooring and surveillance,” according to Trend Micro.
Kaspersky researchers
“Both ours and previous reporting from others have documented TwoSail Junk’s less precise and broad use of forum posts and replies,” Kaspersky researchers, who identified the threat actor as the TwoSail Junk APT, noted. However, researchers noted that there could be a dissident aspect of the campaign: “These forum posts direct individuals frequenting these sites to pages hosting iFrames served from their exploit servers. We add Telegram channels and Instagram posts to the list of communication channels abused by these attackers. These sites and communication mediums are known to be frequented by some activist groups.”
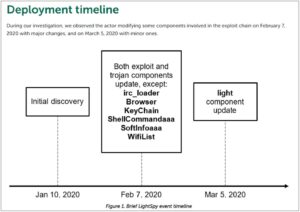
Timeline
The attacks were first identified this January 10 by Kaspersky, and began large scale, via a huge distribution campaign, on February 18. The attacks have continued during March: Trend Micro last week spotted related forum posts that pretended to link to a schedule for protests in Hong Kong.
Source: Kaspersky
Kaspersky meanwhile has observed the APT tinkering with the code on an ongoing basis, modifying some exploit chain components on both February 7 and on March 3 and extending the number of supported devices. Now, the exploits used targets a variety of iPhone models, from the iPhone 6S up to the iPhone X.
“The actor was actively changing implant components,” according to the Kaspersky analysis, which noted that the first observed version of one of the exploits resembled a proof of concept (PoC). “Based on our observations of these changes over a relatively short time frame, we can assess that the actor implemented a fairly agile development process, with time seemingly more important than stealthiness or quality.”
The Watering Holes
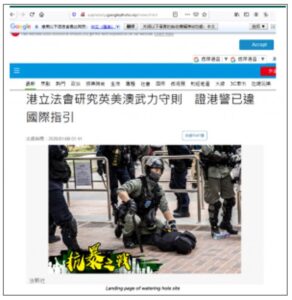
Some of the URLs used in the campaign lead to a malicious website created by the attacker. Kaspersky noted that the initial watering hole site (hxxps://appledaily.googlephoto[.]vip/news[.]html) seen in January was designed to mimic a well-known Hong Kong-based newspaper called Apple Daily. This was done by simply copying HTML content from the original, researchers said.
The site in turn contained three iframes that pointed to different sites, according to the analyses.
Watering-hole landing page. Source: Kaspersky.
“Starting on February 18, the actors began utilising a series of invisible iframes to redirect potential victims to the exploit site as well as the intended legitimate news site from the lure,” Kaspersky researchers wrote.
Trend Micro added: “The only visible iframe leads to a legitimate news site, which makes people believe they are visiting the said site. One invisible iframe was used for website analytics; the other led to a site hosting the main script of the iOS exploits.”
Links to these malicious sites were posted on four different forums, in posts that include the headline of a given news story, accompanying images and a link to the fake news site.
“The topics used as lures were either sex-related, clickbait-type headlines or news related to the COVID-19 disease,” wrote researchers at Trend Micro. “We do not believe that these topics were targeted at any users specifically; instead they targeted the users of the sites as a whole.”
In other cases, a legitimate site was copied and injected with a malicious iframe.
“There are many techniques that attackers can use to compromise websites – SQL injection, cross-site scripting (XSS) and social engineering techniques are the most commonly used,” Trend Micro researcher William Gamazo Sanchez commented. “However, for this particular attack we did not focus on techniques they used against the websites. We have reasons to believe they would employ several techniques, though.”
The Exploit Chain
Once a visitor hits the malicious watering-hole site, the full exploit chain involves a silently patched Safari bug (which works on multiple recent iOS versions) and a customized kernel exploit, researchers said.
The silently patched Safari bug does not have an associated CVE, according to Trend Micro, but its exploitation leads to the exploitation of an infamous, known kernel vulnerability used to gain root privileges.
The flaw (CVE-2019-8605), a use-after-free issue existing in the kernel, could enable a malicious application to execute arbitrary code with system privileges. The flaw allows phones to be jailbroken, in essence. Jailbreaks are useful for those wanting to install custom code, add features or perform security research outside the purview of the Apple ecosystem – but can also expose phones to spyware and malware attacks.
When the kernel exploit (jailbreak) is triggered, a function called payload. Dylib proceeds to download the multiple data exfiltration modules outlined before; as well as functions associated with start-up and loading, and instructions for connecting to the hardcoded location of the command-and-control (C2) server.
The aforementioned “light” function serves as the main control for the malware and is capable of loading and updating the other modules, according to the research.
“[The malware] is a custom job that is very well-designed with a modular architecture,” said Gamazo Sanchez. “More sophisticated than the average malware variant, [especially when it comes to] the level of sophistication to exfiltrate data. Most notably, the actors have clear targets in mind and designed a mechanism and distribution pattern to reach these targets based on their computing habits, to ensure they will not be noticed immediately.”
iPhone users are protected from the malware if they have updated to the latest iOS version.
Links to Android Campaign
The iOS effort appears to be connected to a previous, similar 2019 campaign aimed at Android users, according to researchers at both firms. In that offensive, links to malicious apps were found on various public Hong Kong-related Telegram channels.
That Android malware family was first seen as a calendar app containing protest schedules in Hong Kong. It was disseminated via the “winuxhk” and “brothersisterfacebookclub” Telegram channels and Instagram posts in late November 2019, Kaspersky researchers have noted.
The message lure in Chinese translated to: “The Hong Kong People Calendar APP is online ~~~ Follow the latest Hong Kong Democracy and Freedom Movement. Click to download and support the frontline. Currently only Android version is available.”
Rogue App
Once installed, the rogue app made requests for sensitive permissions, and set about harvesting and exfiltrating contacts, text messages, the user’s location and the names of stored files, researchers said.
The new iOS campaign and the older Android campaign are linked via their infrastructure, according to the Trend Micro analysis: The Android download and C2 servers used the same domain name (hkrevolution[.]club) as one of the watering holes used by the iOS component.
Attribution
While Kaspersky is calling the APT group behind the effort “TwoSail Junk,” researchers there said that the operators are likely tied to other, well-known threat actors.
“We have hints from known backdoor call-backs to infrastructure about clustering this campaign with previous activity,” according to the firm’s analysis. “And we are working with colleagues to tie LightRiver with prior activity from a long running Chinese-speaking APT group, previously reported on as Spring Dragon/Lotus Blossom/Billbug(Thrip), known for their Lotus Elise and Evora backdoor malware.”
For instance, further technical analysis by Kaspersky of the previous Android campaign showed there to be two subzones of the URL used for serving the malicious apps.
“Resolving for C2 resources, we worked with partners to pivot into a handful of “Evora” malware samples…that also use poorgoddaay[.]com subzones for their C2,” Kaspersky noted. “These new Evora backdoors are 99 percent similar as rated by our Kaspersky Threat Attribution Engine to Evora backdoors previously deployed by SpringDragon.”
Evora Malware
The researchers said they also saw other Evora malware samples calling back to these same subnets while targeting specific organizations in Hong Kong – lending further credence to the idea that TwoSail Junk is affiliated with SpringDragon.
“This particular framework and infrastructure are an interesting example of an agile approach to developing and deploying surveillance framework in Southeast Asia,” according to the Kaspersky analysis. “This innovative approach is something we have seen before from SpringDragon, and LightRiver targeting geolocation at least falls within previous regional targeting of SpringDragon/LotusBlossom/Billbug APT, as does infrastructure and Evora backdoor use.”
Trend Micro researchers
For its part, Trend Micro researchers agree that the evidence points to a sophisticated attacker.
“It is safe to say this is not a financially motivated campaign,” remarked Gamazo Sanchez . “There are indicators that this form of attack can be considered sophisticated: Attacks targeting iOS is relatively uncommon over the years given the stringent measures built in in these devices; uses of ‘silent patches’ makes it difficult to find and track known and addressed bugs; an added layer of sophistication is seen with the customization attackers used to match the model and iOS version of the target devices.”
He added that while the campaign, which Trend Micro calls Operation Poison News, is focused on Hong Kong for now, investigations are ongoing into the operators’ future plans. Kaspersky also said that there’s evidence that other versions of the backdoor are under development.
“The userConfig variable indicates other possible platforms that may have been targeted by the same actors, such as Linux, Windows and routers,” according to the analysis.
Beware of sophisticated malware
The technical complexity of the latest threats is challenging for the average DPO, but knowledge of what is currently out there is as ever the key to defence. The motivations behind the perpetrators of these attacks can be debated, but the effects on vital technology potentially, when mankind is finding for its very survival is frightening, and the culprits should be outlaws in every nation.